
Trend Micro shared results from a study that reveals systemic challenges with security integration into business processes. The report includes the top ways to drive engagement and agreement around cybersecurity strategies within an organization.
There will be a surge in dedicated cybersecurity committees in organisations across the world in the next few years, according to new data released today from Gartner.
The National Counterintelligence and Security Center (NCSC) on Monday warned that efforts by the Chinese government to obtain U.S. health data, particularly DNA, through hacking and other means had been stepped up during the COVID-19 pandemic.
Oxfam Australia investigates a suspected data breach after a threat actor claimed to be selling their database belonging on a hacker forum.
It would be safe to say that social media has become an integral part of most of our lives. Be it to make friends, find jobs, seek validation, or simply find an antidote to boredom, these algorithmically-draped platforms can be the perfect breeding ground for social engineering attacks.
Research by Tessian has revealed that every photo we post and tag people, leads to the leak of valuable information that can be abused by hackers to design targeted attacks
Healthcare organizations are still struggling to keep their patients’ confidential data out of the reach of hackers. With the onset of COVID-19, hospitals rushed to provide care to patients, sometimes at the cost of cybersecurity. And, they are still paying for it.
Cybersecurity spending in critical infrastructure has been little impacted by the COVID-19 pandemic, save for some reshuffling on where that spend is most needed. The effect has been mostly in increased demand for secure remote connectivity.
According to a report by ABI Research, cybersecurity spending for critical infrastructure (CI) will increase by $9 billion over the next year to reach $105.99 billion in 2021.
Congress is demanding the National Security Agency come clean on what it knows about the 2015 supply-chain attack against Juniper Networks.
Enhanced Explosive RAT and Caterpillar tools are at the forefront of a global espionage campaign.
Advanced persistent threat (APT) group Lebanese Cedar has compromised at least 250 public-facing servers since early 2020, researchers said, with its latest malware.
Remote work continues to fueling a spike in phishing and cyberattacks, particularly in the U.S.
When it comes to paying the ransom in a ransomware attack, demands are on the rise. Yet, many companies that paid the ransom failed to receive a decryption key, in a survey issued Monday.
Researchers have uncovered two novel Android surveillanceware families being used by an advanced persistent threat (APT) group to target military, nuclear and election entities in Pakistan and Kashmir.
The money being wire transferred by business email compromise victims is on the rise, as cybersecurity criminals evolve their tactics.
The U.S. Department of Justice has indicted three North Korean computer programmers for their alleged participation in widespread, destructive cyberattacks as part of the advanced persistent threat (APT) known as Lazarus Group
New research has found evidence that a Chinese-affiliated threat group (APT31) has hijacked a hacking tool previously used by the Equation Group (which has been tied to the U.S. National Security Agency, or NSA).
Human-rights activists are being targeted by cyberattacks as part of a wider effort by the Vietnamese state to censor anyone speaking out against the government, Amnesty International’s Security Lab alleges.
































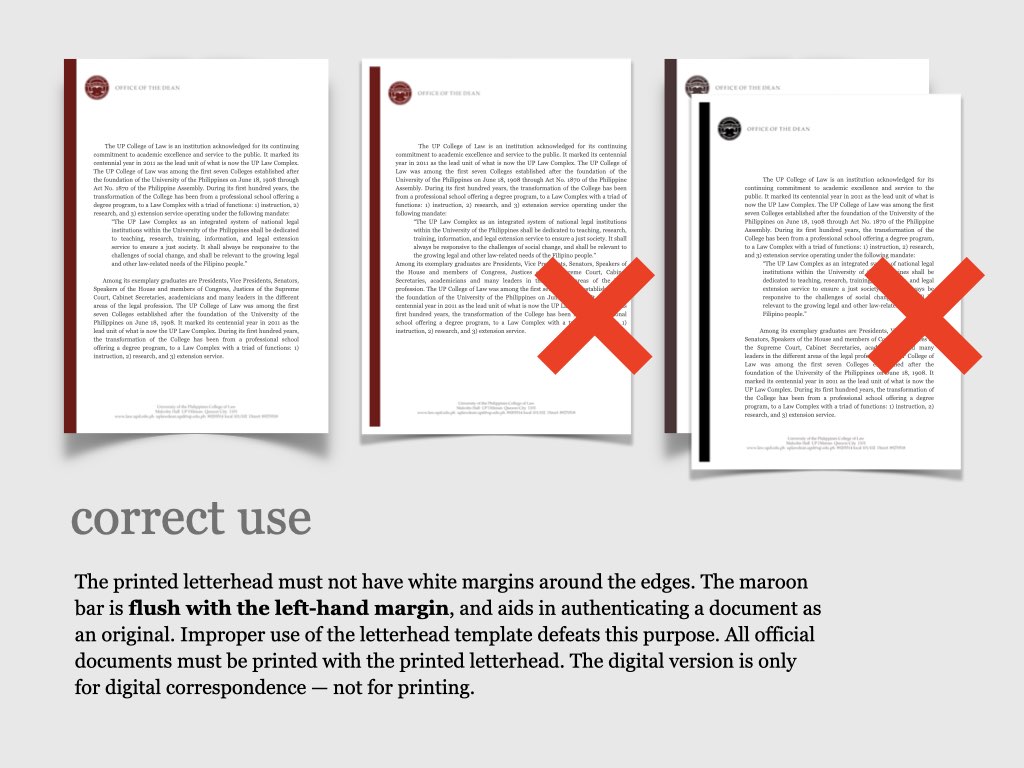
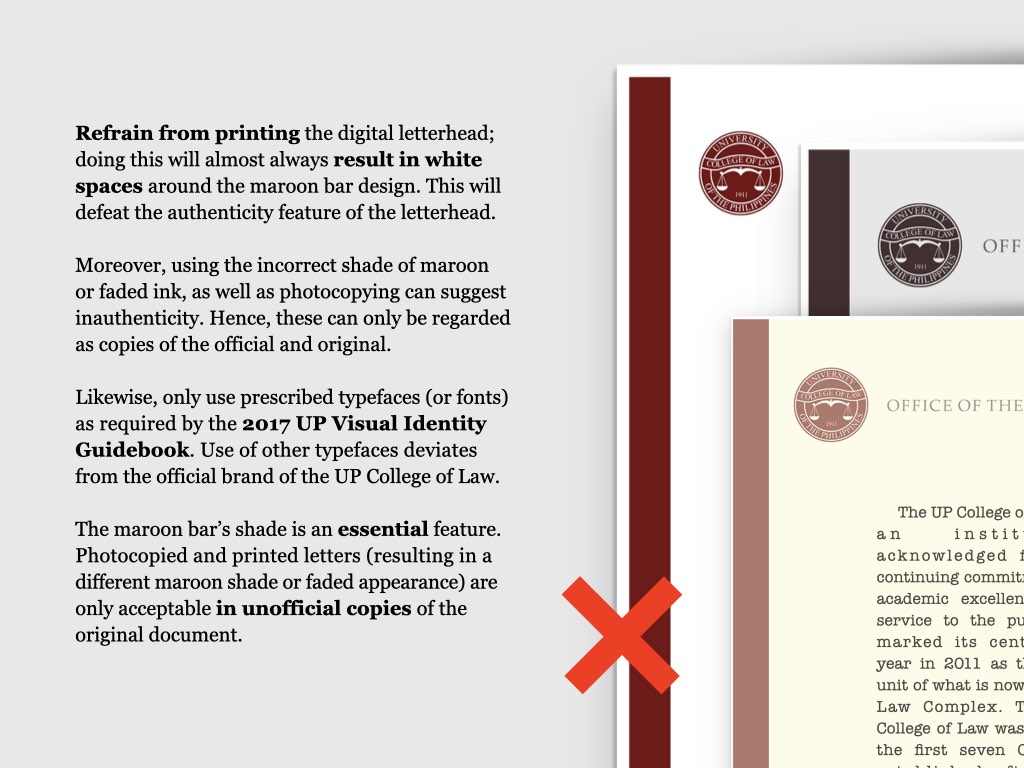


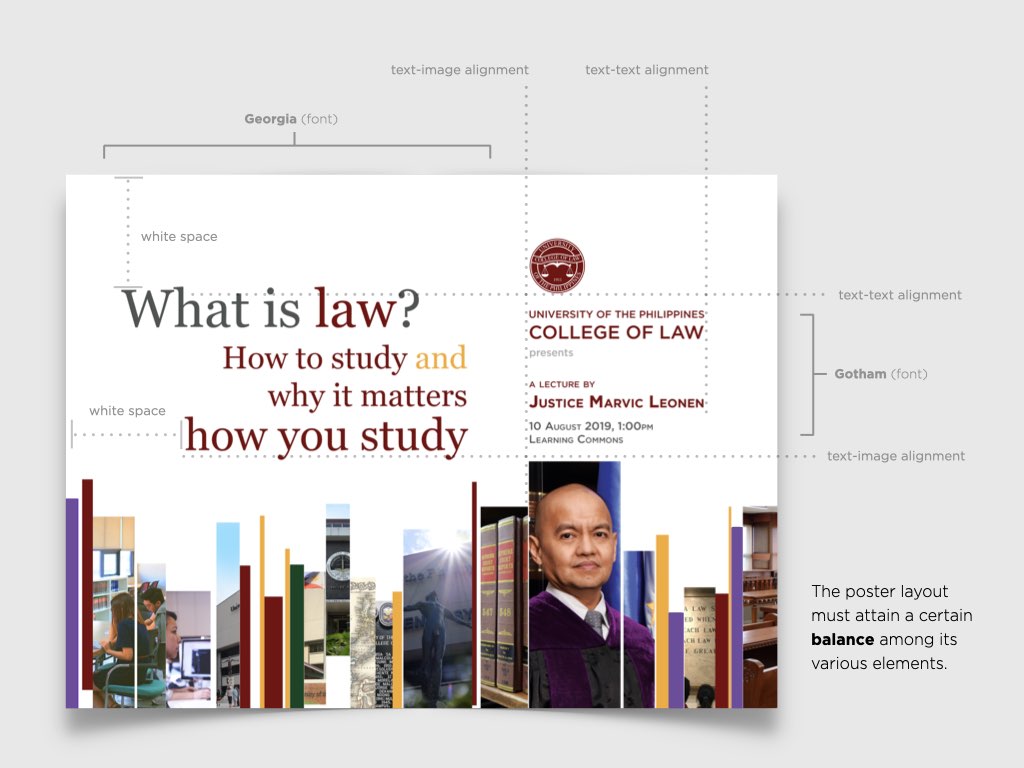







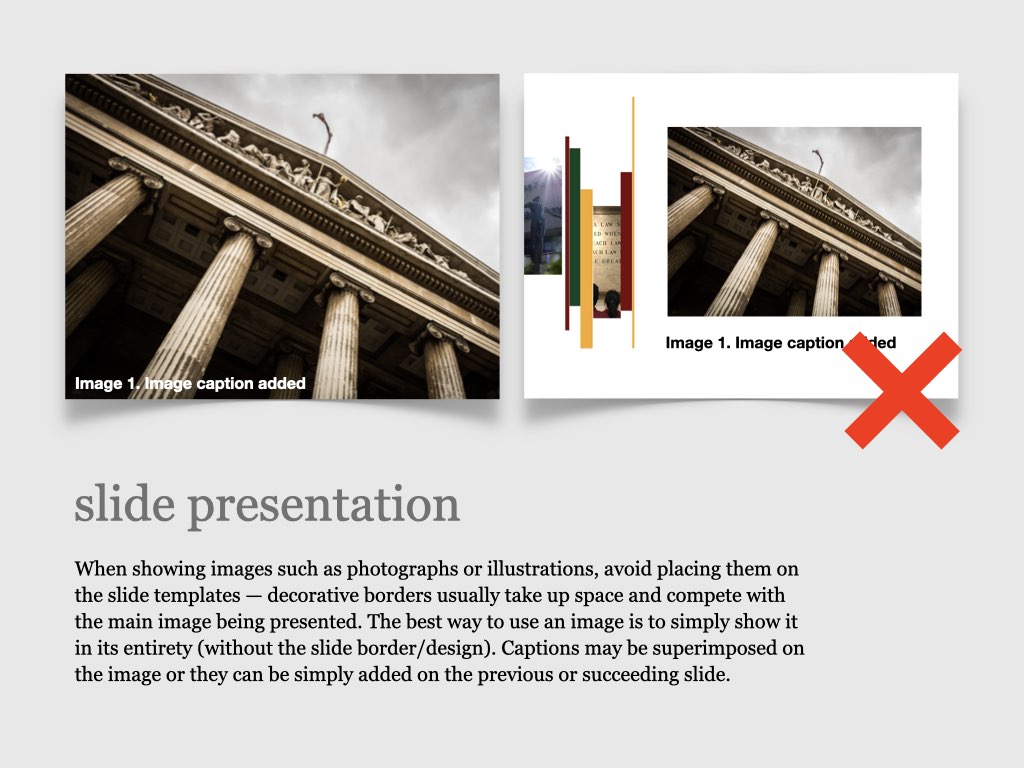
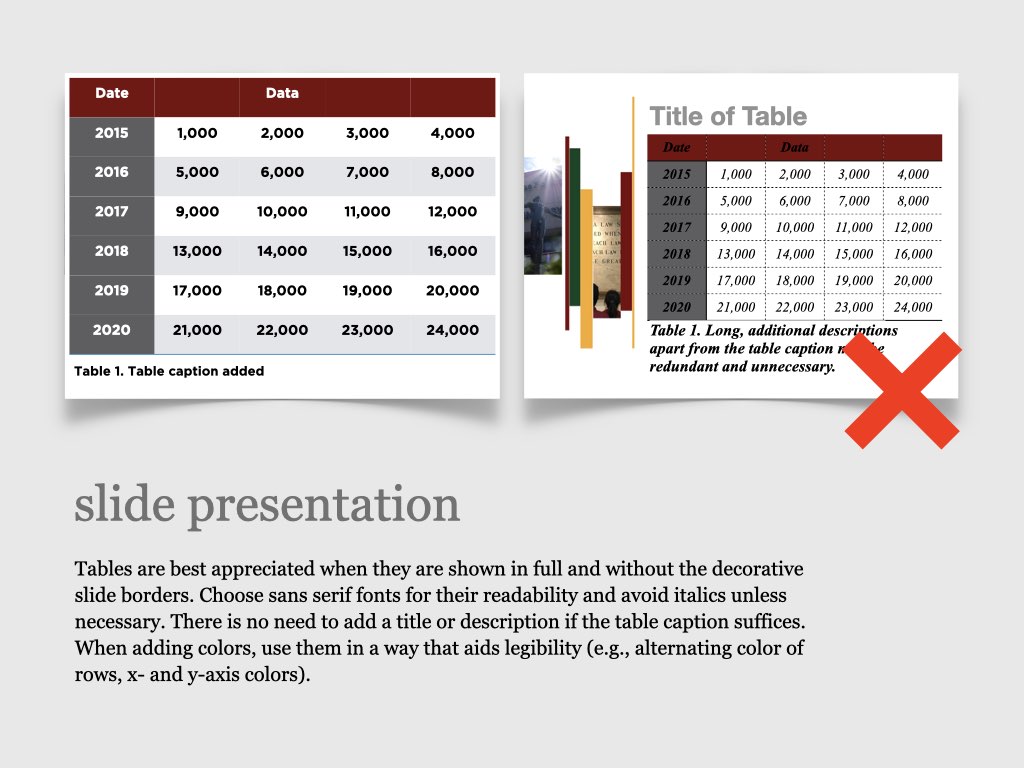












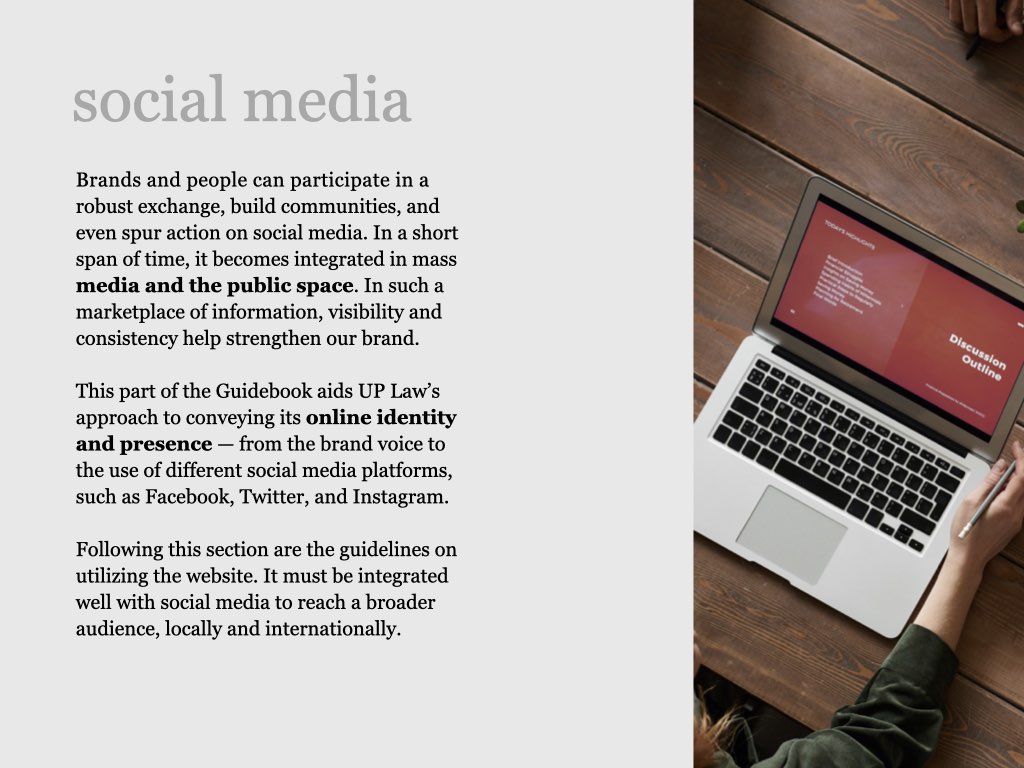










 on the upper right corner to select a video.
on the upper right corner to select a video.